Day 02: Advent of Cyber 2024
Challenge URL
Description
One man’s false positive is another man’s potpourri.
We are given access credentials to a SIEM(Security Information and Event Management system) and are asked to investigate the logs for some suspicious activity.
Solution
After following the instructions to navigate the SIEM, we land at the Discover page with a bunch of logs and some filters.
Let’s use the following filters as the guide suggests.
- host.hostname
- user.name
- event.category
- process.command_line
- event.outcome
- source.ip
We filter the timestamp to November 29, 2024 00:00:00 to December 1, 2024 23:30:00 since that seems to be the breach period.
What is the name of the account causing all the failed login attempts?
To find this we set the following filters:
- event.category = authentication
- event.outcome = failure
We see that the username causing all the failed attempts was service_admin
How many failed logon attempts were observed?
This is just the amount of hits in the logs for the above filters.
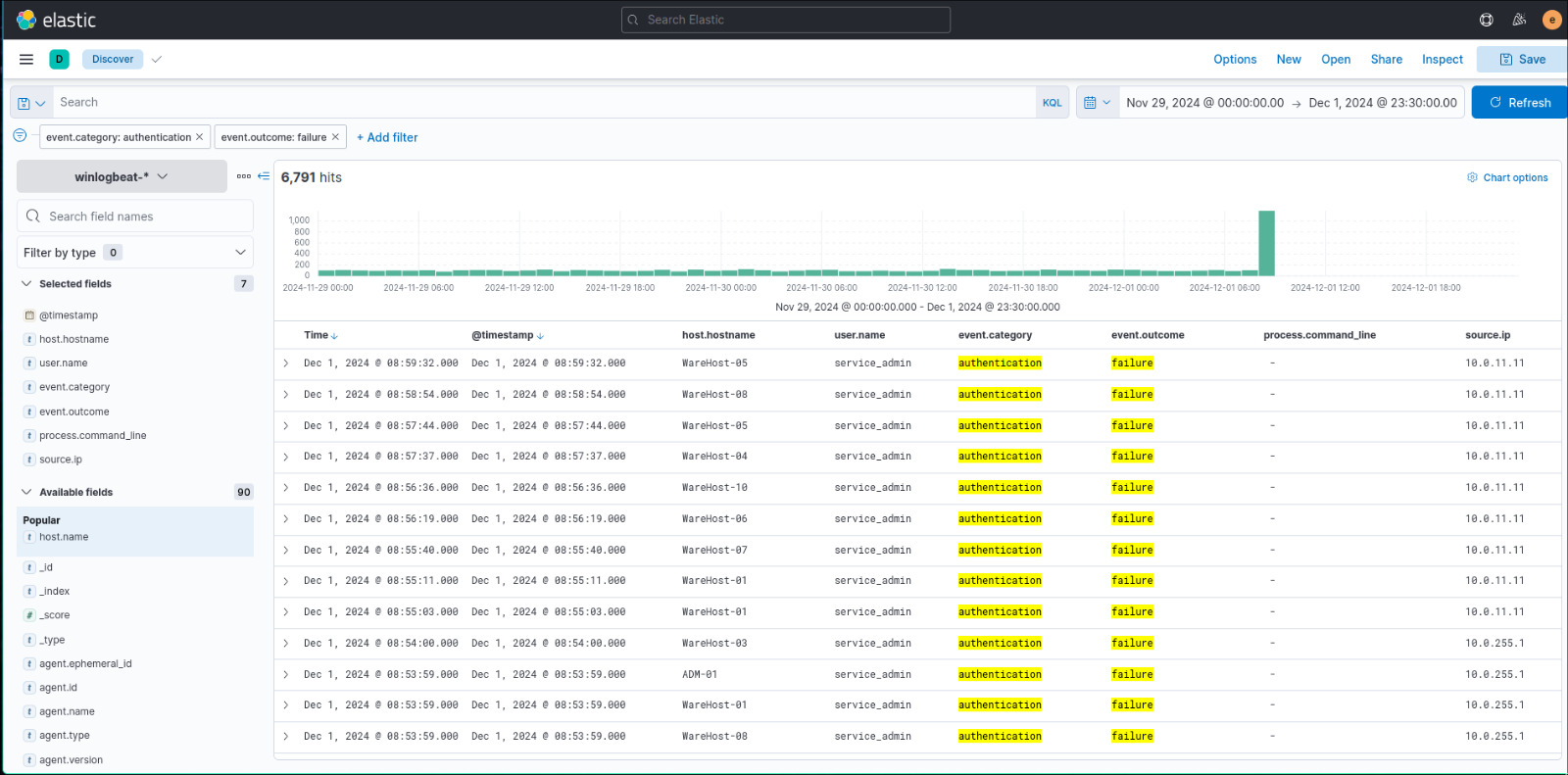
We make it out to be 6,791.
What is the IP address of Glitch?
We see that 2 IP addresses in specific tried to authenticate, 10.0.11.11 and 10.0.255.1
Both have the same username so we see which had prior successful logins and we make out the IP of the Glitch to be 10.0.255.1.
When did Glitch successfully logon to ADM-01? Format: MMM D, YYYY HH:MM:SS.SSS
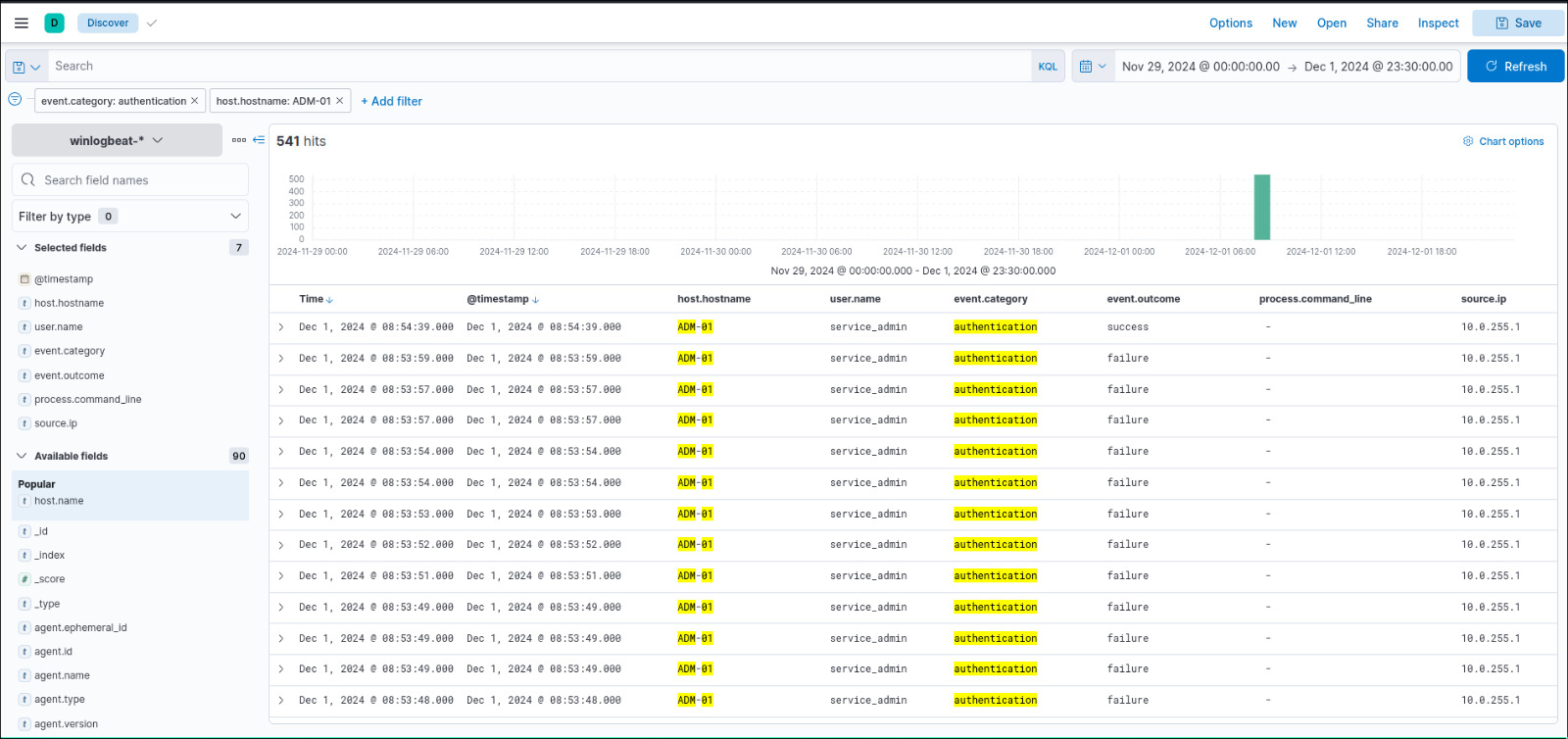
We filter by event.category = authentication and host.hostname = ADM-01 and we see that the latest successful login was on Dec 1, 2024 08:54:39.000
What is the decoded command executed by Glitch to fix the systems of Wareville?
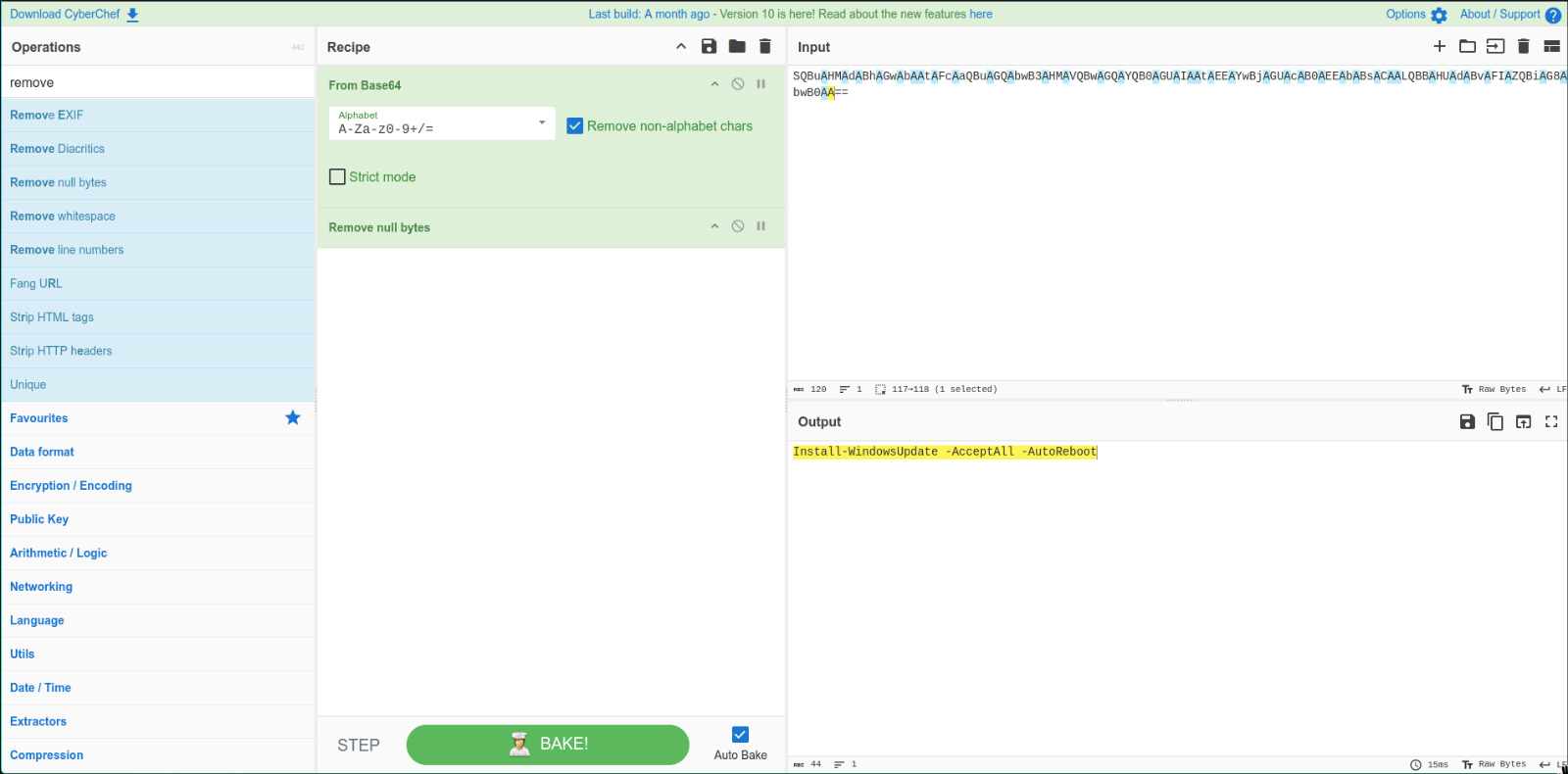
We see the payload for any of the commands executed and after converting from Base64 and sanitization, we make it out to be Install-WindowsUpdate -AcceptAll -AutoReboot.